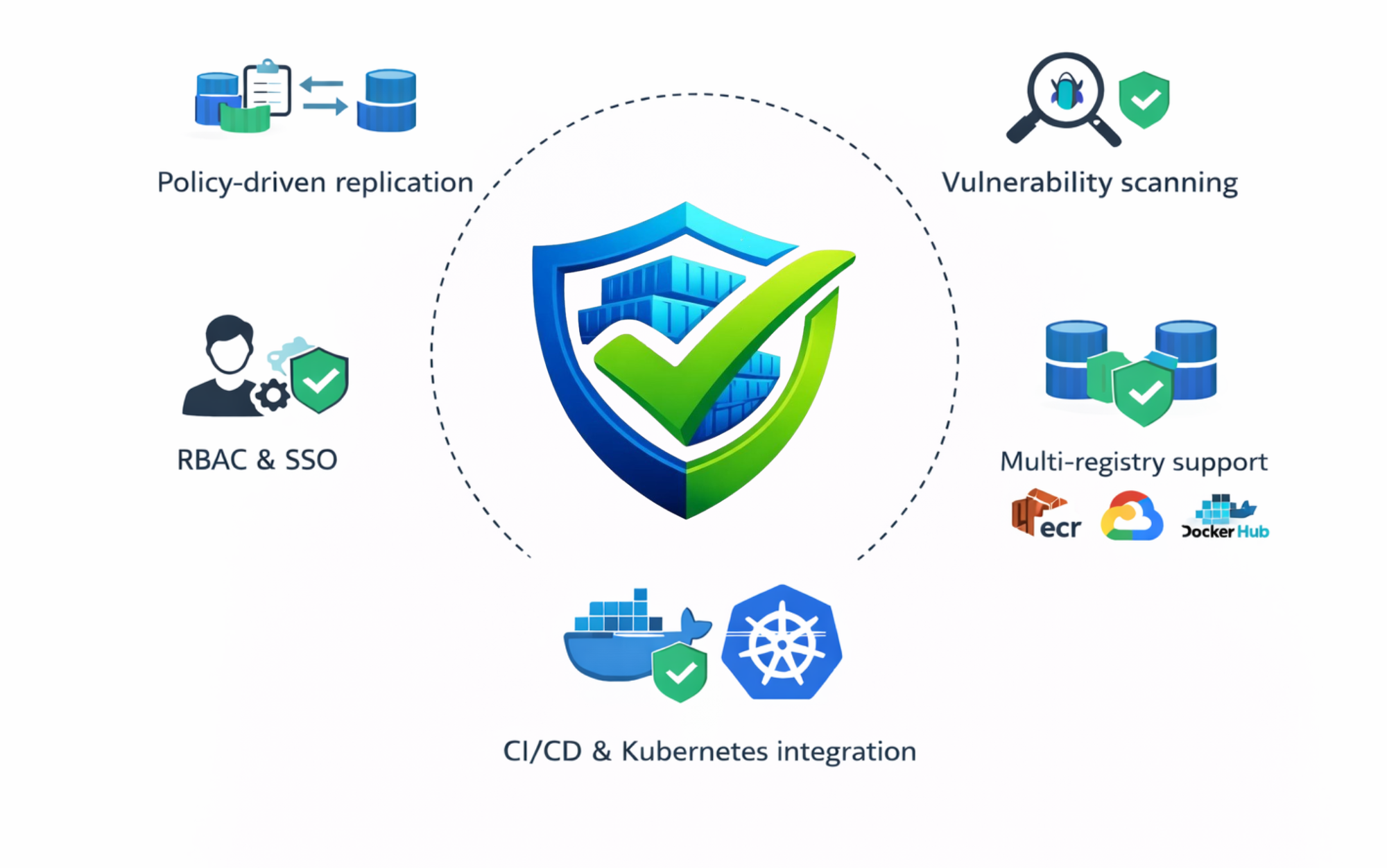
Key Capabilities
-
Project-Based Image Management
Organizes container images into projects with fine-grained access control. -
Role-Based Access Control (RBAC)
Assigns permissions at the project level, from read-only access to full administrative control. -
Policy-Driven Registry Replication
Automatically replicates images across Trustary and external registries using push or pull rules. -
Built-In Vulnerability Scanning
Integrates Trivy and external scanners to detect vulnerabilities through manual or scheduled scans. -
Enterprise Authentication
Supports LDAP/AD and OIDC-based SSO for secure, centralized user management. -
Operational Automation
Includes job orchestration, monitoring dashboards, and automated garbage collection for storage optimization.